INSECURE ATTACHMENTS [link to experiment 2.2]
Winner of NewHive's “Privacy, Surveillance and Prison Reform” award
An ongoing series of experiments questioning the relationship between data and emotional vulnerabilities in the private and public spheres.
Interpersonal vulnerability has been recently embraced in both academic¹ and popular culture² contexts as a quality to be valued and as a potential catalyst for positive outcomes such as intimacy. In contrast, among growing privacy concerns on individual,³ corporate,⁴ and state levels,⁵ the vulnerability of information carries a heavier weight, facilitating opportunities for exploitation. This project seeks to examine the potential outcomes of making both our selves and our data vulnerable.
experiment 1.1 – new methods:
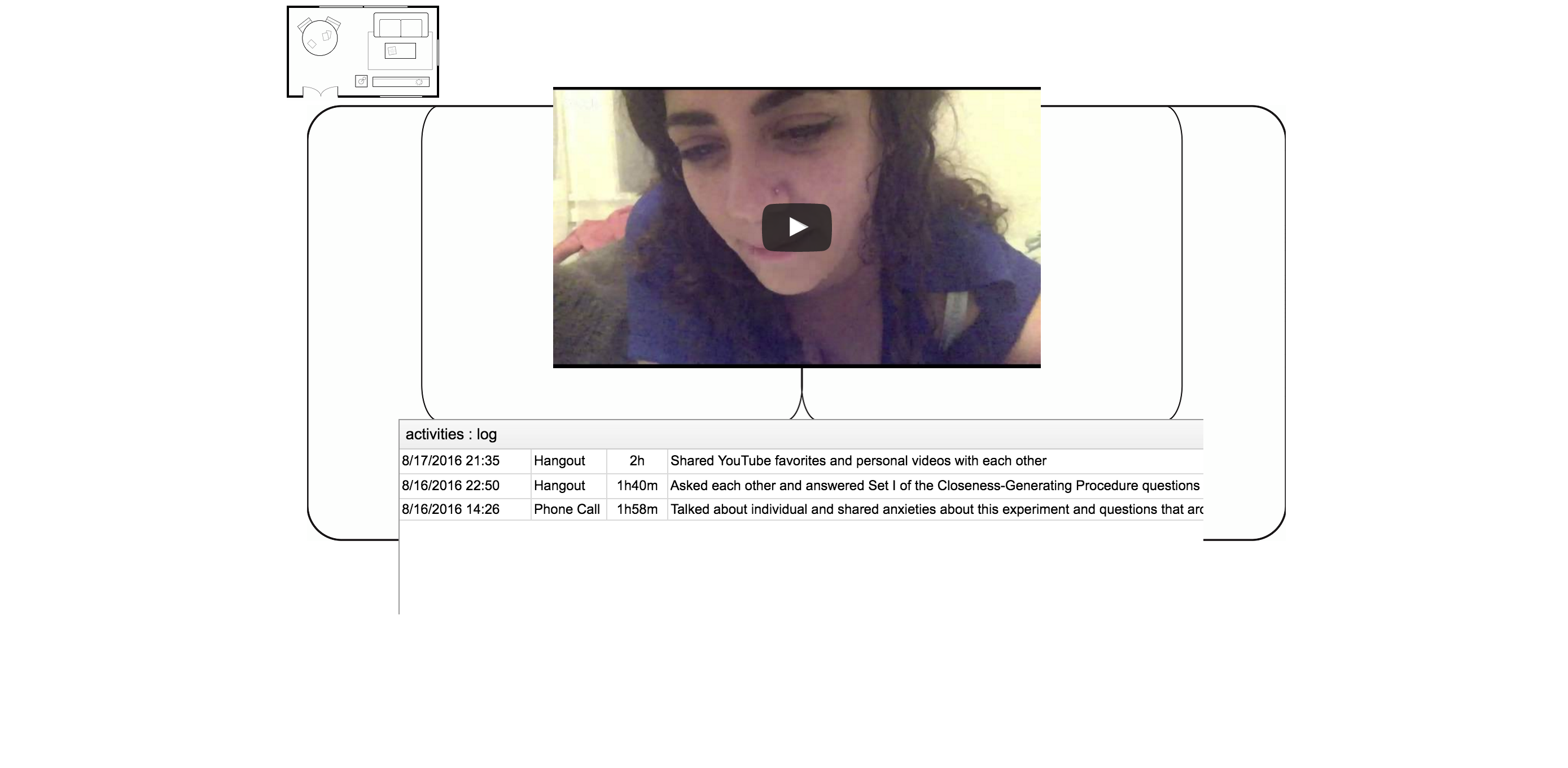
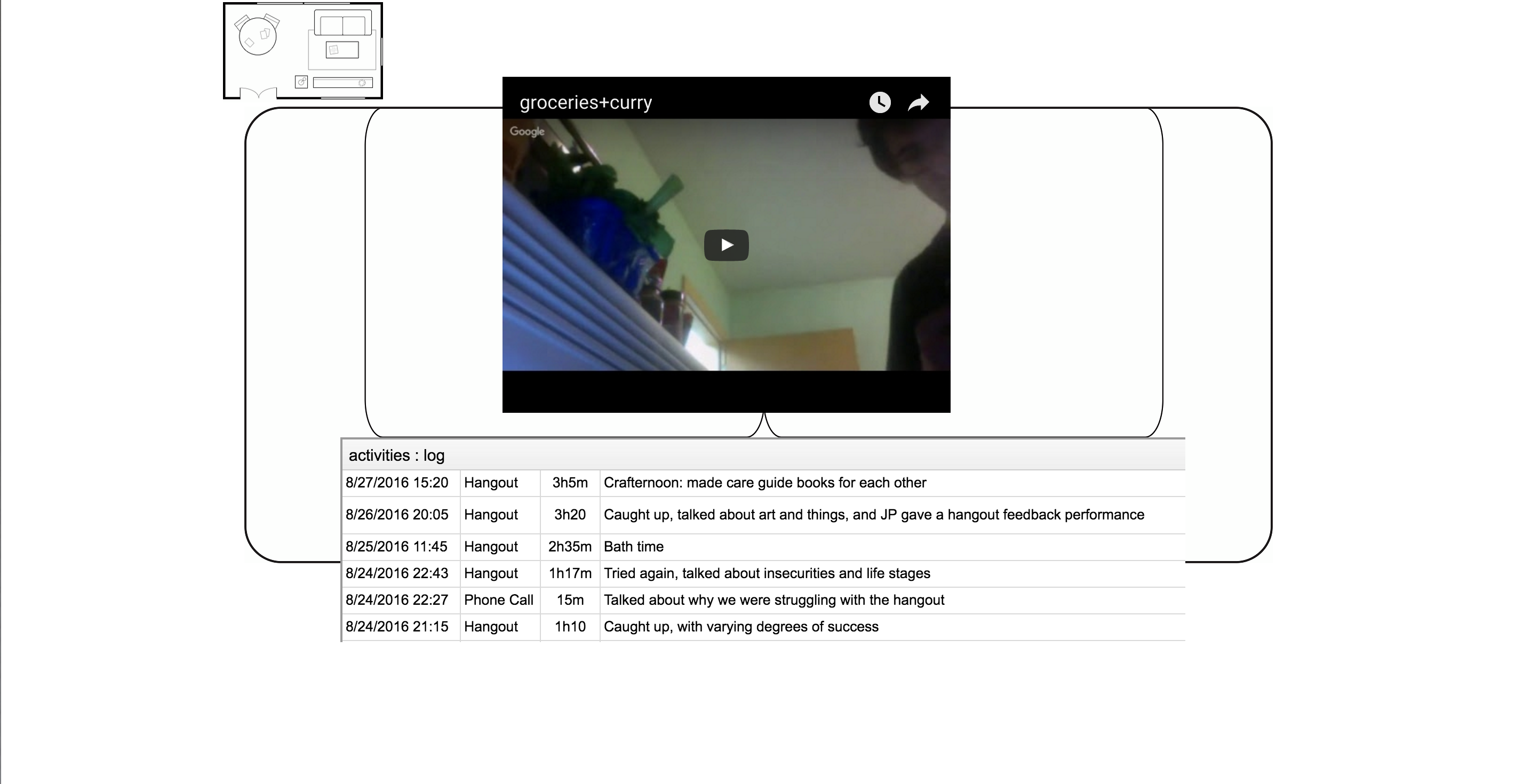
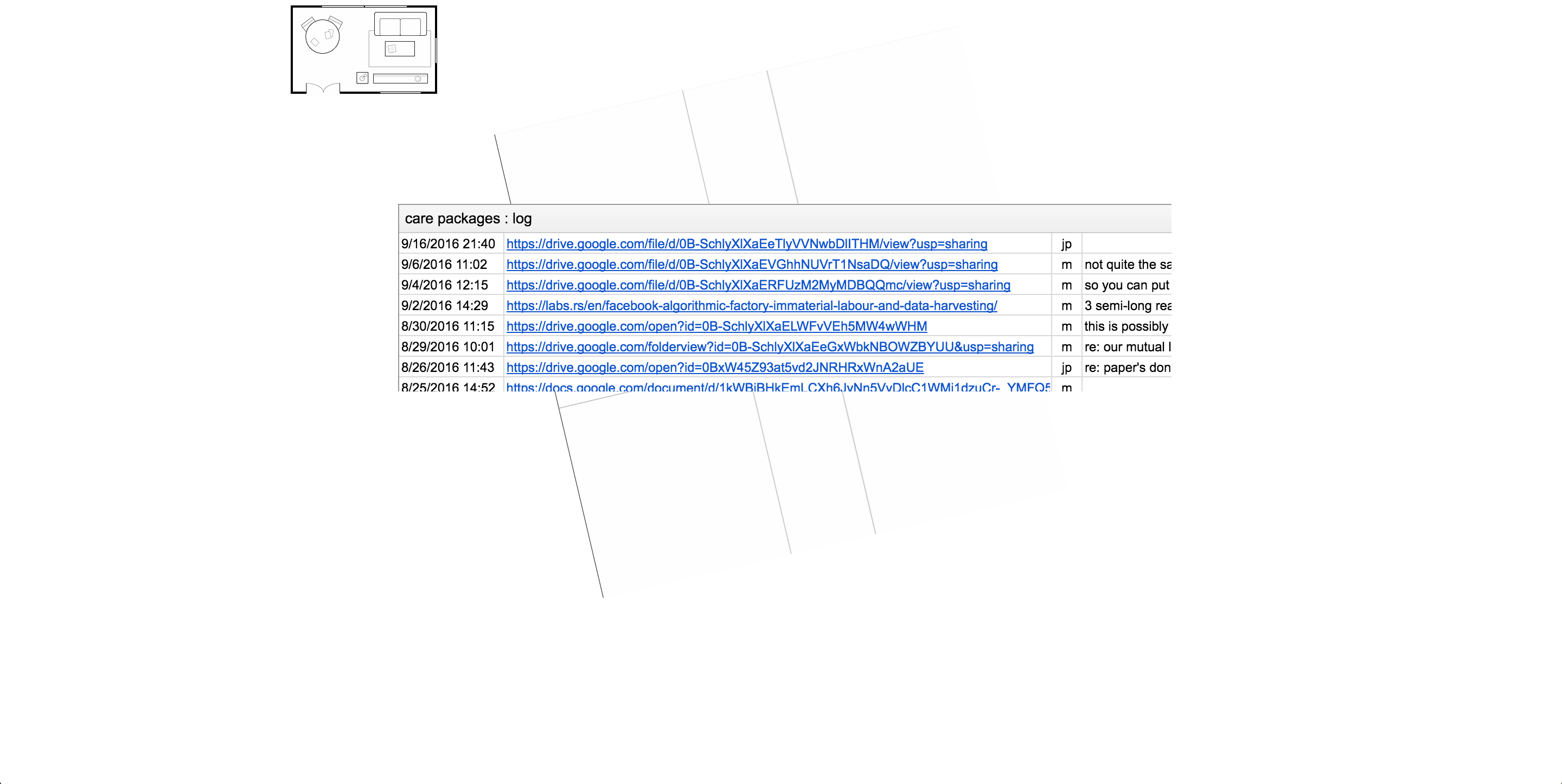
For one month in 2016, the two of us inhabited a digital space, accessible to anyone, as research subjects. Our presence included live-streamed hangouts—during which we attempted and subsequently analyzed a series of progressively vulnerable actions, conversations, and exercises—leaving care packages for one another, and an archive of the data that our mutual activities generated over the course of the month, including the entirety of our text-based communications. We repurposed existing platforms to publish and store our data in order to demonstrate how tedious it is to access one's "own" data through these interfaces, and to share it with as many entities (corporate and governmental) as possible.
Developed in residence at the Welcome to My Guest Room Digital Artist Residency.
experiment 1.2 – preliminary findings on privacy, power, and surveillance:
As we continue to explore channels for furthering this research, we have re-envisioned a static version of the first version of the project on the NewHive platform, where we present it alongside the protocols we used to access and share our data, as well as our preliminary findings on issues of privacy, power, and surveillance which emerged from the study.
_____________________________________________________________________________________________
¹e.g. the work of Aron et. al
²e.g. the work of Brown
³e.g. camfecting, the hacking of webcams
⁴e.g. the organizational doxing of Ashley Madison
⁵The most obvious e.g. being the NSA revelations